Blog
Top 10 Web Application Security Testing Tools [2025]
- August 31, 2023
- Posted by: Pawan Panwar
- Category: Web Application Security

Table of Contents
Top 10 Web Application Security Testing Tools in 2025: Ultimate Guide
Do you have a keen interest in learning web application security testing skills? If yes, then this article is just for you. Here, we will talk about the Top 10 Web Application Security Testing Tools that can offer you the best security environment.
In the end, we have also mentioned one of the most renowned training providers offering a dedicated training & certification program for web application security skills. What are we waiting for? Let’s get straight to the topic!
What Are Web Application Security Testing Tools?
Software programs called web application security testing tools are made to find, examine, and fix security flaws in web applications. They aid in the detection of problems such as broken authentication, SQL injection, and cross-site scripting (XSS).
Acunetix, Burp Suite, and OWASP ZAP are well-known products. Let’s talk about the Top 10 Web Application Security Testing Tools!
Key Features for Web Application Security Testing Tools
Following are some of the key features of web application security testing tools:
1. Comprehensive Vulnerability Scanning: In addition to OWASP Top 10 vulnerabilities (such as SQL injection, XSS, and CSRF) and other basic security problems, the tool should be able to identify a broad variety of online application vulnerabilities.
2. Dynamic Application Security Testing (DAST): To simulate real-world assaults and find weaknesses in the application’s runtime environment, DAST capabilities are crucial.
3. Static Application Security Testing (SAST): Early in the development lifecycle, possible vulnerabilities can be found by analyzing source code using SAST.
4. Integration with CI/ CD Pipelines: Automated security testing is made possible throughout the software development process through seamless integration with continuous integration and continuous delivery (CI/CD) pipelines.
5. Accurate Reporting and Remediation Guidance: Along with concise and useful remedial instructions, the tool should include thorough and accurate reports of vulnerabilities found.
6. API Testing Capabilities: Since APIs are becoming more and more common, the tool should be able to test API security, including data validation, authorization, and authentication.
7. Support for Modern Web Technologies: The most recent web technologies and frameworks, such as web services, single-page applications (SPAs), and contemporary JavaScript frameworks, should be supported by the tool.
8. Low False Positive Rate: The false positive rate of the tool must be extremely low. Security experts will save a great deal of time by doing this instead of wasting it looking into unrelated problems.
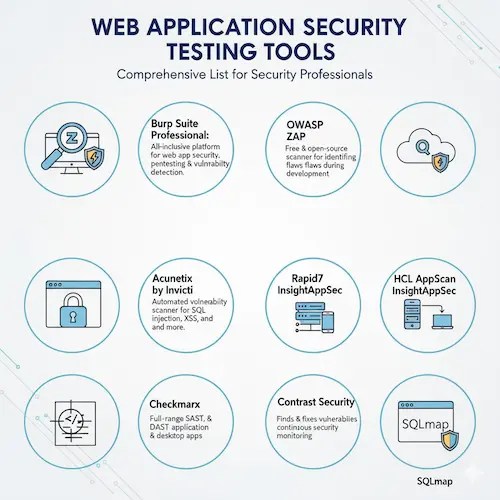
Top 10 Web Application Security Testing Tools For 2025
 h
h
1. Burp Suite Professional:
An all-inclusive platform for doing online application security. It has several capabilities and tools for penetration testing, vulnerability detection, and other tasks.
2. OWASP ZAP (Zed Attack Proxy):
A web application security scanner that is open-source and free. It works quite well at identifying flaws in web applications as they are being developed and tested.
3. Acunetix by Invicti:
SQL injection and cross-site scripting are only two of the many web application vulnerabilities that can be found with the aid of an automated web vulnerability scanner.
4. Veracode:
Offers a variety of options for application security assessment, such as software composition analysis, dynamic analysis, and static analysis.
5. Checkmarx:
This provides a full range of application security testing options, such as interactive application security testing (IAST), DAST, and SAST.
6. Qualys TotalAppSec:
Offers online application scanning as one of its cloud-based security and compliance solutions.
7. Rapid7 InsightAppSec:
A solution for dynamic application security testing (DAST) that finds weaknesses in web apps and APIs.
8. HCL AppScan:
Helps businesses find and fix vulnerabilities in their desktop, mobile, and web apps by offering application security testing solutions.
9. Contrast Security:
It provides solutions for IAST and runtime application self-protection (RASP), which offer ongoing security monitoring and defense.
10. SQLmap:
An open-source penetration testing tool that makes it easier to find and take advantage of SQL injection flaws.
Why Web Application Security Testing Is Crucial in 2025?
Web application security testing is crucial in 2025 for the following reasons:
- Increased Sophistication of Cyberattacks: Traditional security measures are no longer adequate because cybercriminals are always creating more complex attack methods.
- Expansion of the Attack Surface: The attack surface has grown dramatically due to the widespread use of online apps, APIs, and microservices, increasing the likelihood of exploitation.
- Growing Reliance on Web Applications: Web apps are becoming more and more important to both individuals and businesses, which makes them easy targets for hackers.
- Data Breaches and Compliance Requirements: Stricter data privacy laws (like GDPR) require strong security measures because data breaches can cause serious financial and reputational harm.
- API Security Risks: To guarantee their protection, specific testing is necessary because the extensive usage of APIs creates new security flaws.
- Rise of Cloud-Native Applications: Applications that are cloud-native provide particular security challenges that call for specific testing methods and tools.
- Automation and CI/CD Integration: Security testing needs to be automated and incorporated into CI/CD pipelines to identify vulnerabilities early in order to keep up with rapid development cycles.
- Evolving Threat Landscape: Continuous security testing is necessary to keep up with new threats because vulnerabilities are always being found.

Key Benefits of Using Web Application Security Testing Tools
| S.No. | Benefits | How? |
| 1. | Prevention of Data Breaches | Protects sensitive data by identifying and addressing vulnerabilities that can result in illegal access and data exfiltration. |
| 2. | Protection of Customer Trust and Reputation | Shows a dedication to security, building client trust, and avoiding reputational harm from security events. |
| 3. | Reduced Financial Losses | Prevents expensive downtime, legal costs, and fines from the government that come with security incidents and data breaches. |
| 4. | Compliance with Regulatory Requirements | Assists businesses in fulfilling regulatory requirements and industry standards like GDPR, HIPAA, and PCI DSS. |
| 5. | Early Detection of Vulnerabilities | Finds security problems early in the development process, enabling prompt rectification and lowering the expense of later vulnerability fixes. |
| 6. | Improved Application Performance and Stability | Performance snags and stability problems brought on by flaws or malicious code can be found via security testing. |
| 7. | Enhanced Business Continuity | Ensures that web apps continue to function and be available, reducing interruptions and preserving business continuity. |
| 8. | Mitigation of Business Risk | Proactively fixes security flaws that can jeopardize vital company resources and operations. |
How to Choose the Best Web Security Testing Tool?
You can choose the right security testing tool by considering the following factors:
- Specific Testing Needs: Determine the necessary testing kinds (DAST, SAST, IAST, and API testing) and make sure the tool fully addresses them.
- Integration Capabilities: Check if the product works with the development and deployment processes you currently use, such as CI/CD pipelines and other security technologies.
- Accuracy and Reporting: Assess the tool’s precision in locating vulnerabilities and its capacity to deliver concise, useful results along with remedial instructions.
- Scalability and Performance: Examine the tool’s scalability to accommodate future requirements as well as its capacity to manage the volume and complexity of your web applications.
- Vendor Support and Expertise: Examine the vendor’s track record, level of support, and proficiency in web application security testing.
Common Challenges in Web Application Security Testing
| S.No. | Challenges | Why? |
| 1. | Rapidly Evolving Technologies | Testers must constantly upgrade their knowledge and resources due to the rapid development of new web technologies and frameworks. |
| 2. | Complexity of Modern Web Applications | With their various microservices, APIs, and structures, modern online apps are difficult to test thoroughly. |
| 3. | False Positives and Negatives | Security testing technologies may produce false negatives, which overlook important vulnerabilities, or false positives, which waste effort. |
| 4. | Integration with CI/ CD Pipelines | It can be difficult to incorporate security testing into CI/CD pipelines that move quickly. |
| 5. | API Security Testing | It takes certain tools and knowledge to test the security of APIs, which are becoming more and more important to web applications. |
| 6. | Maintaining Test Coverage | It can be challenging to provide thorough test coverage across all program features and components. |
| 7. | Resource Constraints | Some organizations might not have the time, finances, or expertise to devote to security testing. |
| 8. | Keeping Up with the Threat Landscape | Because cyber dangers are constantly evolving, it is necessary to continuously study and adjust to new attack methods. |
Final Thoughts: Choosing the Best Tool for Your Needs
Now that we have talked about the Top 10 Web Application Security Testing Tools, you might want to get the best testing experience from experts. For that, you can get in contact with Craw Security, one of the most reputable VAPT service providers in the IT Industry.
Craw Security offers the best experience for Web Application Penetration Testing Services in India to several sectors working in the IT industry. They even use the latest web application security testing tools for testing the level of security measures. What are you waiting for? Contact, Now!
Frequently Asked Questions
About Top 10 Web Application Security Testing Tools
1. What is web application security testing?
The practice of assessing a web application to find security flaws and make sure it is safe from possible attacks is known as web application security testing.
2. Why is security testing important for web applications?
Security testing is important for web applications for the following reasons:
- Protection of Sensitive Data,
- Prevention of Financial Losses,
- Maintenance of User Trust,
- Compliance with Regulations, and
- Ensuring Business Continuity.
3. Which security testing tool is best for beginners?
Because of its user-friendly design and free, open-source nature, OWASP ZAP is frequently suggested as a fantastic place for newbies to start.
4. Are free web security testing tools reliable?
Although some free web security testing tools have useful capabilities, their dependability varies, and they might not have all the features and support of paid alternatives.
5. How often should I perform web security testing?
To handle new vulnerabilities, web security testing should be done often, ideally during the software development lifecycle and continually in production.
6. Can automated security testing tools replace manual penetration testing?
Because complicated vulnerability research and exploitation require human skill, automated security testing methods cannot completely replace manual penetration testing.
7. What are the most common web application vulnerabilities?
The following are some of the most common web application vulnerabilities:
- Broken Access Control,
- Cryptographic Failures,
- Injection,
- Cross-Site Scripting (XSS), and
- Security Misconfiguration.
8. How do I choose the right security testing tool for my business?
You can choose the right security testing tool for my business:
- Define Your Specific Needs,
- Assess Integration & Compatibility,
- Evaluate Accuracy & Reporting,
- Consider Scalability & Performance, and
- Evaluate Vendor Support & Expertise.
9. Do web security testing tools affect application performance?
Yes, by mimicking actual assaults, web security testing tools, particularly dynamic analysis tools, can impact application performance and could result in brief lags or interruptions.
10. Which tool is used for web application security testing?
Depending on the particular testing requirements, a variety of tools are employed, such as Acunetix, OWASP ZAP, and Burp Suite.
11. What is the best DAST tool?
Although the “best” DAST tool varies depending on the demands, Burp Suite Professional and Acunetix by Invicti are frequently praised for their accuracy and extensive feature set.
12. What is the best SAST tool?
The ultimate “best” SAST tool is a subjective decision that greatly depends on the needs of the particular company. Nonetheless, a few tools are regarded as industry leaders and frequently garner great reviews.
13. What is the tool to check website security?
Website security can be checked with a variety of tools that serve different purposes.
Related Blogs
Role of AI in Cybersecurity: Beneficial or Detrimental?
Expert Training in Cyber Forensics Investigation
The 10 Essential Steps of Effective Penetration Testing
Exploring the World of Ethical Hacking
Related
Leave a ReplyCancel reply
About Us
CrawSec, commonly known as Craw Security is a paramount cybersecurity training institution situated at Saket and Laxmi Nagar locations in New Delhi. It offers world-class job-oriented cybersecurity training programs to interested students.
Contact Us
1st Floor, Plot no. 4, Lane no. 2, Kehar Singh Estate Westend Marg, Behind Saket Metro Station Saidulajab New Delhi – 110030
+91 951 380 5401
[email protected]
HR Email : [email protected]
Trending Cyber Security Courses
One Year Cyber Security Course | Basic Networking with AI | Linux Essential | Python Programming | Ethical Hacking | Penetration Testing with AI | Cyber Forensics Investigation | Web Application Security with AI | Mobile Application Security with AI | AWS Security with AI | AWS Associate with AI | Red Hat RHCE | Red Hat RHCSA | Red Hat Open Stack | Red Hat RH358 | Red Hat Rapid Track | Red Hat OpenShift | CCNA 200-301 | CCNP Security 350-701 | CompTIA N+ | CompTIA Security+ | CompTIA Pentest+ | CompTIA A+ | CompTIA Cysa+ | CompTIA CASP+ | Pen-200 / OSCP | Pen-210 / OSWP | Reverse Engineering | Malware Analysis | Threat Hunting | CRTP | CISA | Certified Ethical Hacker(CEH) v13 AI | Certified Network Defender | Certified Secure Computer User | Eccouncil CPENT | Eccouncil CTIA | Eccouncil CHFI v11
Are you located in any of these areas
NARELA | BURARI | TIMARPUR | ADARSH NAGAR | BADLI | RITHALA | BAWANA | MUNDKA | KIRARI | SULTANPUR MAJRA | NANGLOI JAT | MANGOL PURI | ROHINI | SHALIMAR BAGH | SHAKUR BASTI | TRI NAGAR | WAZIRPUR | MODEL TOWN | SADAR BAZAR | CHANDNI CHOWK | MATIA MAHAL | BALLIMARAN | KAROL BAGH | PATEL NAGAR | MOTI NAGAR| MADIPUR | RAJOURI GARDEN | HARI NAGAR | TILAK NAGAR | JANAKPURI | VIKASPURI | UTTAM NAGAR | DWARKA | MATIALA | NAJAFGARH | BIJWASAN | PALAM | DELHI CANTT | RAJINDER NAGAR | NEW DELHI | JANGPURA | KASTURBA NAGAR | MALVIYA NAGAR | R K PURAM | MEHRAULI | CHHATARPUR | DEOLI | AMBEDKAR NAGAR | SANGAM VIHAR | GREATER KAILASH | KALKAJI | TUGHLAKABAD | BADARPUR | OKHLA | TRILOKPURI | KONDLI | PATPARGANJ | LAXMI NAGAR | VISHWAS NAGAR | KRISHNA NAGAR | GANDHI NAGAR | SHAHDARA | SEEMA PURI | ROHTAS NAGAR | SEELAMPUR | GHONDA | BABARPUR | GOKALPUR | MUSTAFABAD | KARAWAL NAGAR | GURUGRAM | NOIDA | FARIDABAD
Craw Cyber Security (Saket and Laxmi Nagar) is just a few kilometer’s drive from these locations.


 h
h